Hackers can be real jerks.
A new form of malware has been developed to imitate decryption software that is supposed to help people who have already been victims of
According to a new from Bleeping Computer, the ransomware–which claims to decrypt files affected by the ‘STOP Djvu’ ransomware–actually double-encrypts files, making victims’ problems even worse. The virus, called “Zorab”, was discovered by Michael Gillespie, the creator of the ID Ransomware service.
Hmm, someone released a decryptor for ?
Oh wait… it’s more fucking . Don’t trust anything you find online saying it can decrypt Djvu unless it is from ME. This is just one example of the shaddy shit victims are falling for when they don’t believe me.
— Michael Gillespie (@demonslay335)
Zorab compounds existing problems
Imagine: for years, encrypting ransomware has been a nightmare scenario for unwitting computer users. They click the wrong link, or open the wrong email, and suddenly find themselves in a situation in which all of their files–their most precious photos, the novels they’ve been working on, their musical projects, their work–is encrypted; the ransomware claims that only way to decrypt it is to pay a huge fee.
Of course, there have been anti-malware tools that have been developed to decrypt files without paying exorbitant amounts of money: this is exactly what this new malware is imitating. It claims to help victims of ransomware decrypt their files for free, and then double-encrypts them.
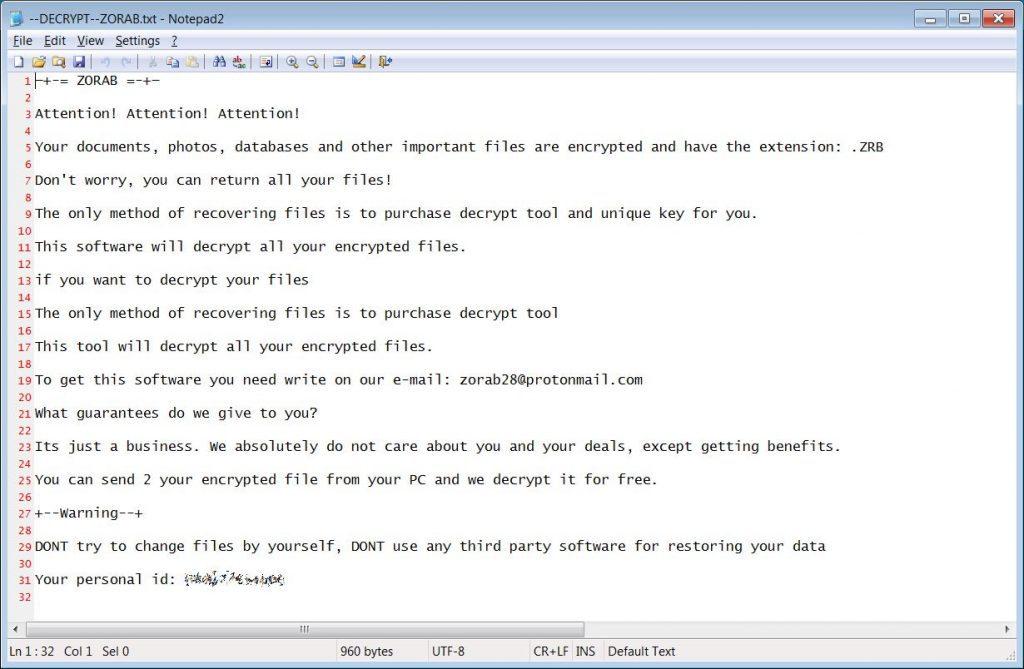
Indeed, when the victim downloads opens one of these fake decryption “tools” and clicks on “Start Scan,” the software extracts an executable file called crab.exe–the Zorab ransomware itself. Once executed, the tool will encrypt all files present on the device with a .ZRB extension.
Zorab also creates ransom notes named ‘–DECRYPT–ZORAB.txt.ZRB’ that are present in each of the folders it encrypts; this note contains instructions on how to contact the ransomware operators for payment instructions.
“We absolutely do not care about you and your deals, except getting benefits,” the notes read.
In a way, the creators of Zorab were quite clever: STOP Dvju is thought to be one of the most prolific–if not the most prolific–pieces of ransomware on the books. Therefore, creating a fake decryption tool for STOP is a quick and easy way to spread another piece of ransomware.
While it hasn’t gotten as much media attention as other pieces ransomware that targets high-net-worth individuals and organizations (such as Maze, REvil, Netwalker, and DoppelPaymer), there are roughly 600 STOP ransomware submissions a day to the ID-Ransomware ransomware identification service.
Bleeping Computer described STOP as “the most actively distributed ransomware over the past year.”
The publication also said that Zorab is currently being analyzed, and that victims should not pay the ransoms that are being demanded of them until it is confirmed that there is no way to exploit weaknesses in Zorab’s software.





Be First to Comment